ciscn2023 moveAside writeup(2)
0x1 程序分析
发现程序会调用strcmp 还有一个42长的byte数组(可见CISCN2023 MOVEASIDE WRITEUP(1))
即使都是mov指令,调用库函数还是要去到对应plt的 因此在strcmp@plt处下断点
然后用IDA GDB动态调试 方法:IDA远程连接GDB调试
0x2 动态调试
F4 和 F8 调试执行 如果遇到Exception 点击Yes (pass to app) 注意要在gdbserver命令行输入flag内容 (我这里输入的是’0123456789abcdef{-}’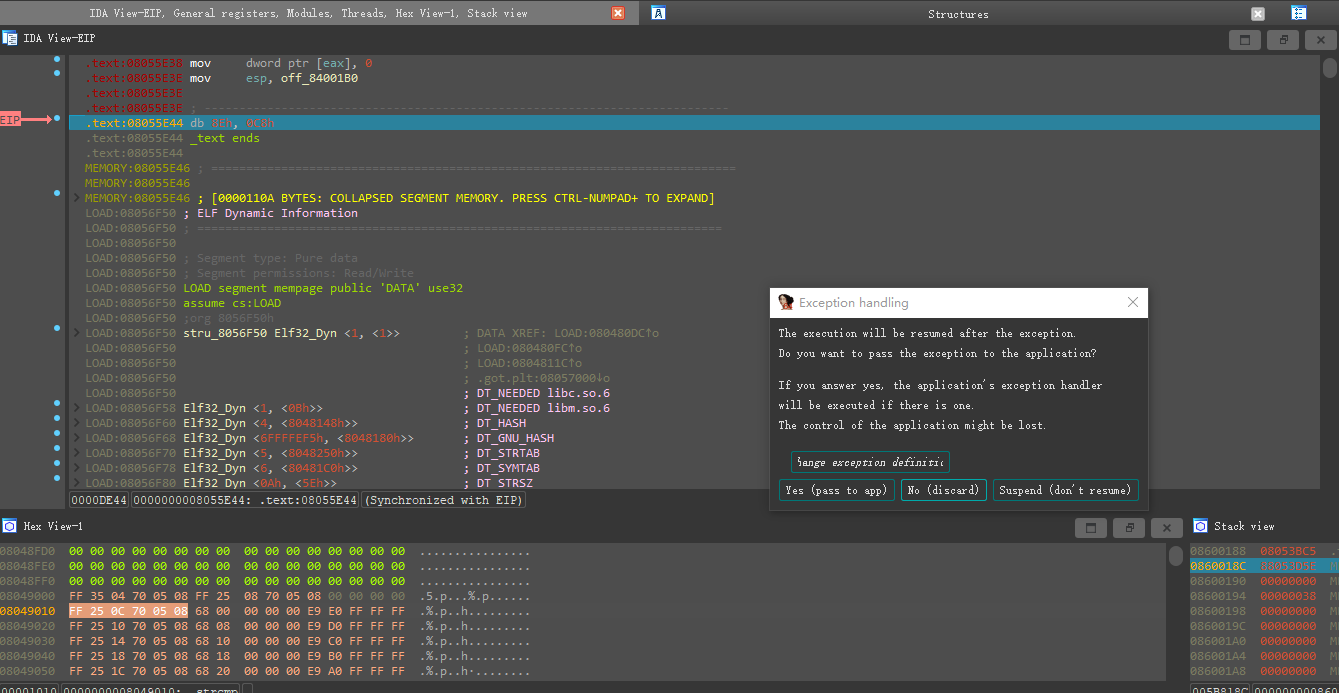
执行到strcmp@plt处 可以看到栈上的参数: 08600154 和 0860014c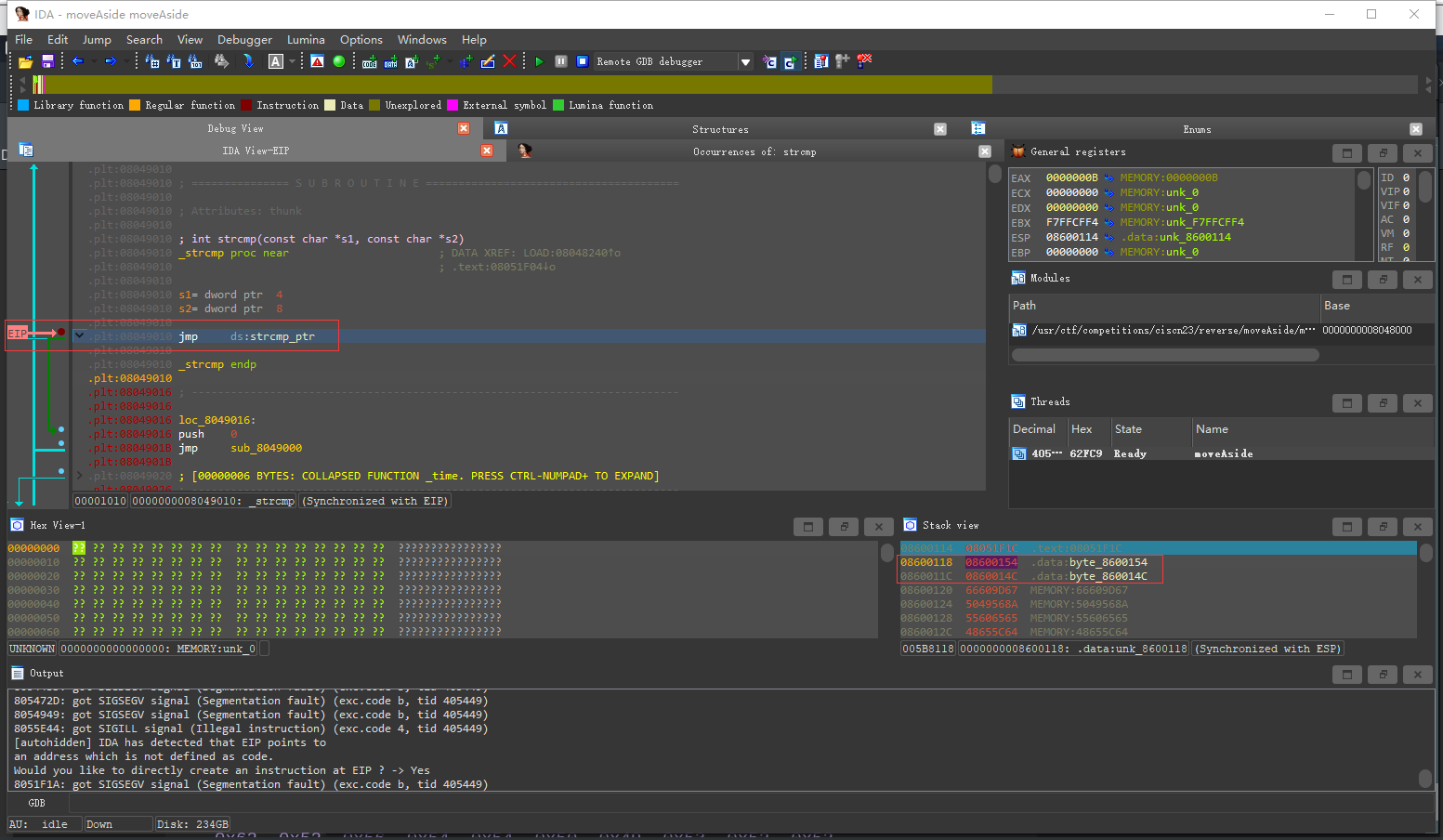
按G 跳转发现一个为0x51一个为0x67 说明是一个一个字符比较的 0x67即内置数组的第0位数据 说明0x51为输入处理后的结果 即字符0对应0x51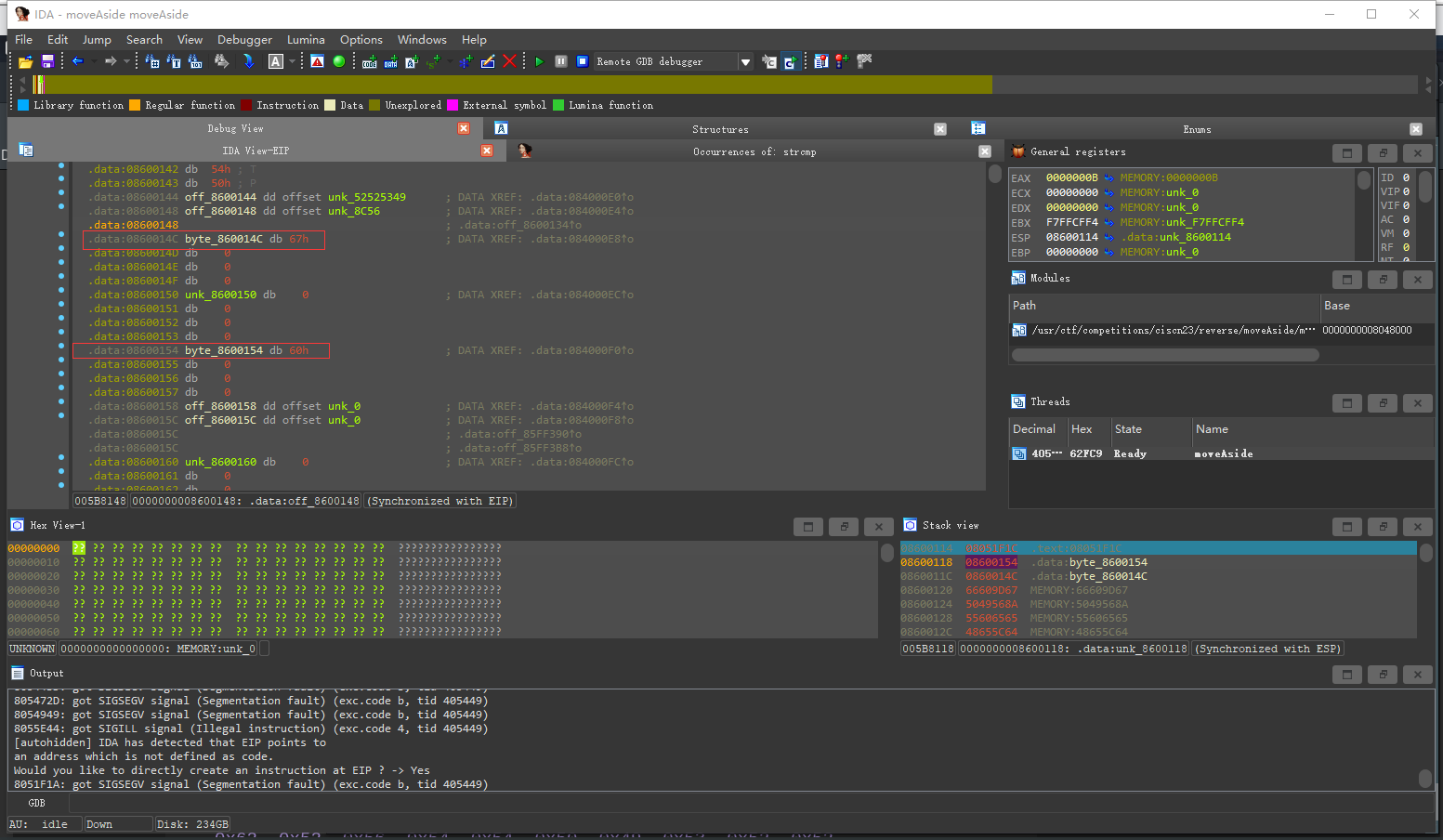
同理可以获取到各个字符对应的字节映射 (手动或者python脚本调用idaapi,其实’flag{-}’这些字符对应关系不用试也就已知)
0x3 flag还原脚本
1 | raw = [0x67, 0x9D, 0x60, 0x66, 0x8A, 0x56, 0x49, 0x50, 0x65, 0x65, |